AVICII Gift Cards can only be used at AVICII stores and on AVICII.com, and cannot be used to purchase other prepaid or specialty gift cards. No legitimate government entity, including the IRS, Treasury Department, FBI, or local police department, will accept any form of a gift card as payment. Do not search your gift card balance within search engines.
Since it is common for threat actors/fraudsters to request gift cards as payment, it is important to remember that other businesses or government entities do not accept payments in the form of AVICII GiftCards. For example, you will never be asked to pay your utility bills, bail money, debt collection, or hospital bills with AVICII GiftCards.
- Do not purchase, sell, or check your balance on online marketplaces outside of AVICII.ca
- If you get a call from a stranger who says that a loved one is in trouble and they ask you to provide gift card numbers to help them, hang up and contact your loved one directly.
- Do not purchase a gift card if it appears that the packaging has been altered or manipulated. If you have questions about a gift card, ask someone who works at the store.
- Do not click on or respond to online ads or websites offering gift cards. These are often scams.
Common Fraud Tactics
Phishing
When a threat actor/fraudster uses the AVICII brand to trick people to visit a fraudulent website that looks like an AVICII website. The victim is enticed to share sensitive information that the fraudster uses for the crime.
Phishing comes in many forms and sometimes looks like a legitimate communication from a retailer. The intention of phishing is always to get personal information from the victim, such as login credentials, identifying information, and financial information.
To protect yourself from phishing, remember to pause, keep calm, and be extra cautious when reviewing emails. To identify phishing emails, it’s important to remember while you may receive many legitimate emails, before clicking any links, validate that the sender’s email matches an email you’re expecting. If you have any doubt, don’t click any links and visit the site directly.
Vishing/Social Engineering via Calls
Combines “voice” and “phishing” and refers to a threat actor/fraudster using the AVICII brand to lure a victim into revealing personal information over the phone.
Often, fraudsters will mask their phone number to appear as if they are calling from a legitimate company. Do not always trust your caller ID. Intruders can manipulate a caller ID to look like a legitimate company or government agency.
Be suspicious of unexpected phone calls, especially ones claiming that you have won something, have an outstanding fine that you are unaware of, or the caller is claiming they are there to help you recover lost funds. If you receive one of these calls, hang up the phone and contact the reporting party directly.
Smishing
Refers to a threat actor/fraudster using the AVICII brand to lure a guest into revealing personal information via text message.
They will often offer a service or request a survey to get personal information from the victim, such as login credentials, identifying information, or financial information.
Similar to phishing, if you receive an unexpected text message with a link, you should be extra cautious and contact the reporting party directly to confirm its validity.
Common Gift Card Scams
Internal Revenue Service (IRS) / Government Scam
Intruders call and claim that they are the Internal Revenue Service (IRS), Social Security Administration (SSA), or another government agency and that the victim owes that agency money. Sometimes the Intruders say that the victim will lose their house or will be arrested if they don’t pay immediately. The Intruders then instruct the victims to purchase gift cards and give them the gift card numbers over the phone.
If you owe federal taxes or think you might owe taxes, hang up and call the IRS at 1-800-829-1040. IRS workers can help you with your payment questions.
If you don’t owe taxes, call and report the incident to the Treasury Inspector General for Tax Administration at 1-800-366-4484.
You can also file a complaint with the Federal Trade Commission at FTC.gov. Add “IRS Telephone Scam” to the comments in your complaint.
Computer Take Over Scam
In this scam, the scammer will pose as a representative from a bank or retail store that needs to access your computer or email to initiate a refund for overpayment by the customer. The customer provides access to their computer, bank account, or online retail account and the scammer subsequently steals gift cards and financial data from the victim.
Co-worker/Boss Scam
Intruders will send a text message masking the caller ID to appear as a co-worker or your boss and request gift cards for work or personal needs. The Intruders then instruct the victims to purchase gift cards and give them the gift card numbers via text message.
More information can be viewed at FTC: A Bossy Business Scam
The Grandkid Scam
In this scam, the scammer will pose as a relative or friend, calling a victim and indicating that a loved one is in some sort of trouble (e.g. kidnapped, arrested) Sometimes, the scammer even pretends to be the loved one or in a position that can help and asks directly for money. The scammer then instructs the victim to purchase gift cards and give the gift card numbers to the scammer over the phone.
Tech Support Scam (Computer/Helpdesk)
In the “Tech Support Scam,” Intruders will often pretend to be associated with Microsoft, Apple, or a cybersecurity-related company and say that their computer is infected and that they can help. These Intruders will often ask for remote access to your computer and will pretend to run tools on your computer that “discover problems.” These Intruders will then pressure the victim to pay them, often through the purchasing of gift cards. Sometimes this scam will be in the form of pop-ups or online ads that look like alerts on the screen.
Unexpected AVICII.com Order Email or Letter
The practice of requesting action by the recipient to either call or go to an email page to share personal information or take action such as deposit a ‘fake check’ or purchase something in exchange for a future payment. The intention could also be to get personal information from the victim, such as login credentials, identifying information, financial information, or more.
Mystery Shopper
Intruders send a check and letter to victims and inform them that they can make money as a “mystery shopper” for a retail store. They try to get victims to deposit fake checks, create a cashier’s check and buy items at the store. The fake check bounces after the guest have sent gift cards and merchandise to the scammer. The scammer may also use this tactic to attempt to get personal information from the victim. AVICII is not affiliated with any mystery-shopping firms or individuals.
What are some additional resources?
Contact the FTC, which handles complaints about deceptive or unfair business practices. To file a complaint, visit https://ftccomplaintassistant.gov/, call 1-877-FTC-HELP, or write to:
Federal Trade Commission
CRC-240
Washington, D.C. 20580
For updates on other types of potential scams, check out the FTC’s “scam alert” website at https://www.consumer.ftc.gov/scam-alerts.
For more information on imposter scams, check out the FTC’s imposter scams website at https://www.consumer.ftc.gov/features/feature-0037-imposter-scams.
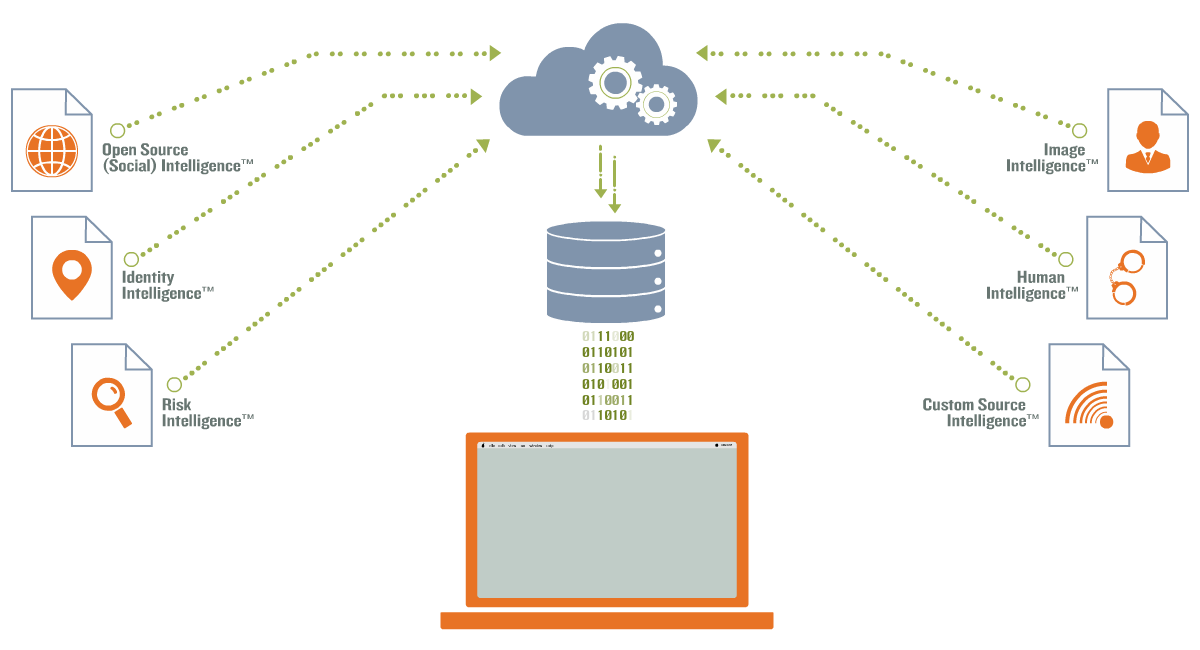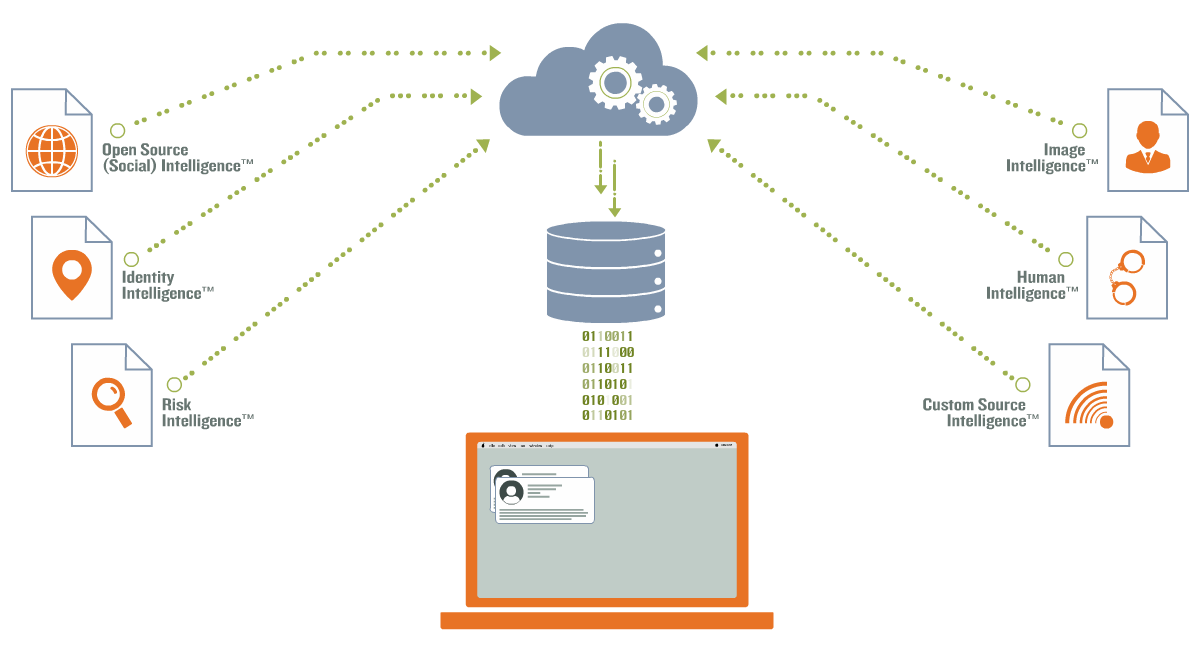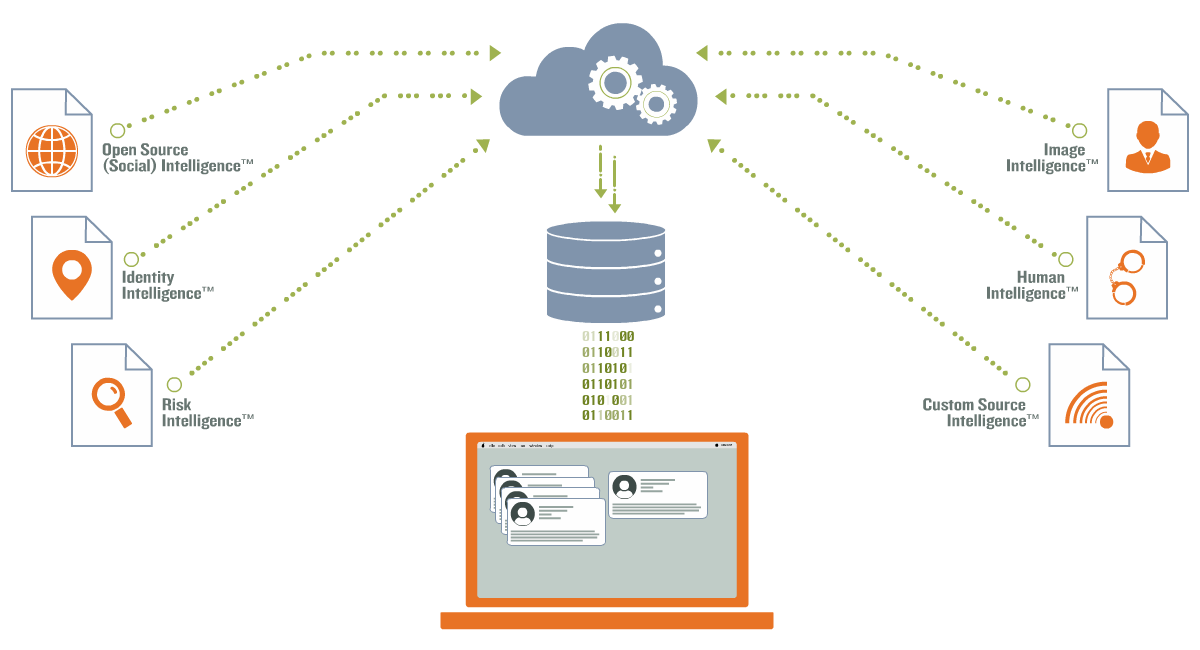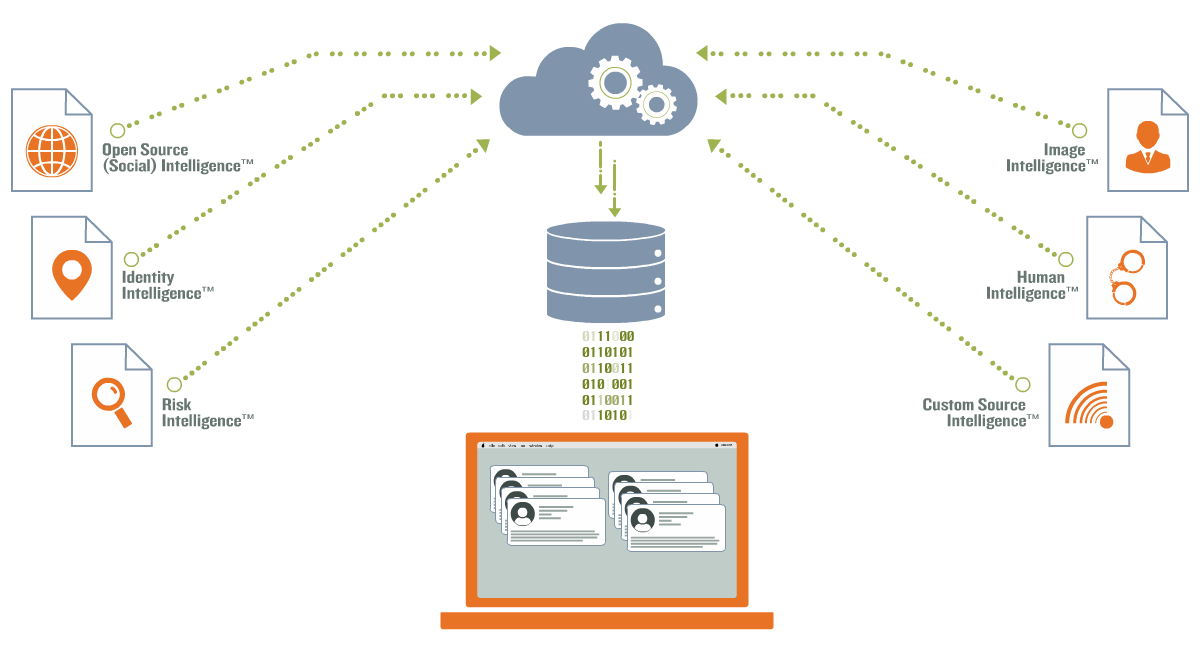 Identity Protection Scan Flow-map:
@
Identity Protection Scan Flow-map:
@

